Teknoloji tüm hızıyla ilerlemeye devam ediyor. Son kullanıcı cihazlarındaki gelişmelerden yapay zeka uygulamalarına, günlük hayatımıza dokunan otomasyon teknolojilerinden uzay teknolojilerine kadar bir çok alanda çok hızlı bir ilerlemeye şahit oluyoruz. Gün içerisinde kullandığımız uygulamalar, çeşitli şekillerde giriş uygulamaların sayısı göz ardı edilmeyecek şekilde arttı. Sosyal medya hesaplarından, e-posta hesaplarına, bulut depolama sistemleri hesaplarına ve oyunlar için bağlandığımız hesaplara kadar bir çok hesaba giriş yapıyoruz ve bu uygulamaların, sistemlerin sayısı her geçen gün artıyor.
Kişisel olarak deneyimlediğimiz bu teknolojik gelişmeler elbette kurumsal bilişim sistemlerinde de kendini gösteriyor. Bugün geldiğimiz noktada kurumsal bilişim sistemleri ve yazılımlar da her geçen gün büyümekte ve kurumsal yapı içerisinde çeşitlenmekte. Çalışanlar işleri için gün içerisinde çok sayıda uygulamaya bağlanıyor ve bu uygulamaların üzerinde çalışıyor. Çalışma verimliliğini artıran bu uygulamaların sayısının ve kompleksliğinin artması kullanıcıların hesap bilgilerinin yönetilmesini de zorlaştırmakta ve bir noktada kullanıcı hesaplarının, kimliklerinin ve yetkilerinin yönetilme ihtiyacını doğuruyor. Bu yazıda kurumsal yapılardaki bu ihtiyaca çözümler sunan kimlik yönetimi kavramı üzerinde duracağız.
Kimlik Yönetimi Sistemi (IDM) Nedir?
Identitiy Management ifadesinin kısaltması olan IDM ifadesi; bütüncül erişim ve kimlik yönetimi (IAM-Identitiy and Access Management) yaklaşımının bir parçasını oluşturan kimlik yönetimi sistemi anlamına gelmektedir. Bütüncül erişim ve kimlik yönetimi yaklaşımı kimlik veri tabanı sistemleri (LDAP, ActiveDirectory, Postgresql vb.kuruluşa özel veri tabanları ), kimlik yönetimi sistemi (IDM) ve erişim yönetimi sistemlerini kapsar ( SSO, CAS, OAuth Erişim ve yetkilendirme (AAA) sistemi yapan yazılımlar). IDM sistemleri veri tabanları ile erişim yönetimi sistemleri arasında konumlanarak kurumsal yapılarda, farklı kimlik veri tabanlarında bulunan kimlik bilgilerini organize eder ve kullanım senaryolarına göre erişim sisteminin kullanımına sunar.
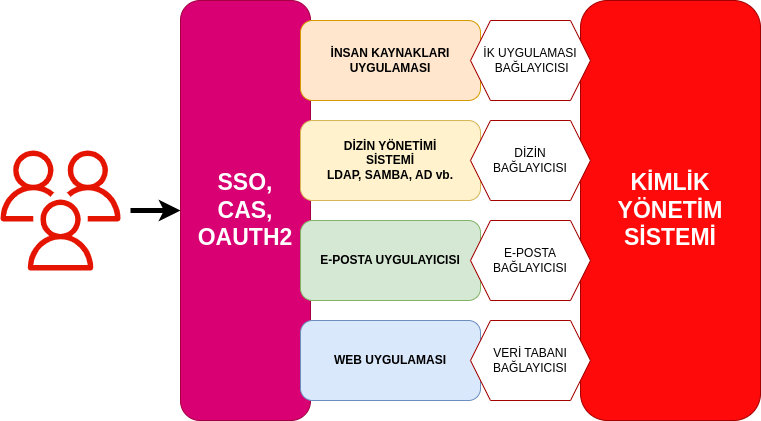
Kimlik Yönetimi Sistemi, kurumsal yapılarda, kimlik bilgilerini üzerinde tutan sistemlerle iletişim kurar. İletişim kurulan sistemlerine örnek verecek olursak; dizin sistemleri, insan kaynakları sistemleri, e-posta sistemleri, ERP yazılımları vb. sistemler sayılabilir. Kimlik Yönetimi Sistemi bu sistemlerle kurduğu iletişim ile; yeni hesapların, kimliklerin ve yetkilendirmelerin merkezi olarak yönetilmesini sağlar. Gerektiği durumlarda okuma, yazma ve senkronize etme gibi bir çok işlem yapabilmektedir.
Kimlik Yönetimi Sistemi IDM Sistemi Avantajları Nelerdir?
Yüksek sayıda kullanıcısı bulunan kurumsal yapılarda kimlik bilgilerinin düzenlenmesi, değiştirilmesi, ekleme/çıkarma işlemleri sistem yöneticileri açısından iş yükü oluşturmaktadır. Her bir kimlik veri tabanına dokunulması gereken senaryolarda birden fazla teknik personel ilgili işlem için zaman ayırmakta ve koordine olmaktadır. Örneğin bir çalışan işten çıktığında kurumsal yapı içerisinde yer alan bütün kimlik veri tabanlarından bilgilerinin silinmesi gerekir. Örneğin bir kullanıcı işten ayrıldığında kurumun Active Directory yöneticisi, İnsan kaynakları veri tabanını yöneten personel, evrak yönetimi sistemini yöneten personel vb bir çok veri tabanındaki kimlik bilgilerini silmek için zaman harcar. IDM bu işlemlerin tek bir merkezden otomatize olarak gerçekleştirilmesini sağlar.
Harcanan zamanın ötesinde kullanıcı kimlik bilgilerinin doğru şekilde yönetilmesi siber güvenlik açısından büyük önem taşımaktadır. Örneğin işten atılan bir personelin kurumsal yapıda kullanılan sistemlerdeki kimlik bilgilerinin silinmemesi durumunda, bu kişi tarafından kurumsal sistemlere erişim sağlayarak zarar vermesi mümkün olacaktır. Gerektiği durumlarda siber güvenliğin sağlanması için istenen sayıda kullanıcının kurumsal sistemlere erişimini tek noktadan hızlı bir şekilde kesmek Kimlik Yönetimi Sistemiyle mümkün olmaktadır. Bu avantajlarının yanında kimlik bilgileri ve yetkilendirmeler ile ilgili denetimler ve bilişim yöneticilerinin incelemesi amacıyla rapor hazırlamak IDM tarafından kolayca gerçekleştirilebilmektedir.
Kimlik Yönetimi Sistemlerinin doğrudan kendi özellikleri sayesinde sağladığı avantajların yanında, kurumsal yapılarda Kimlik Yönetimi Sisteminin devreye alınması sırasında mevcut hesaplardaki, yetkilerdeki ve süreçlerdeki belirsizliklerin ve eksikliklerin ortaya çıktığı tecrübeyle sabittir. Kimlik Yönetimi Sistemi devreye alınmadan önce yapılan analizlerde veya devreye alma sonrası ortaya çıkan bu gibi durumlar düzeltilerek kurumsal yapı içerisindeki kimliklerin, yetkilerin ve süreçlerin olması gerektiği gibi düzenlenmesi sağlanmaktadır.
Özetlemek gerekirse Kimlik Yönetim Sistemlerinin avantajları şunlardır;
- Kurumsal Kimlik Yönetimini Kolaylaştırır
- İş Yükünü Azaltır
- Siber Güvenliğe Katkı Sağlar
- Kimlik, Yetki ve Kullanıcı Süreçlerini Netleştirir
Engerek Kimlik Yönetimi Sistemi Sistemi
Günümüzde ticari yazılım ve sistemlere alternatif olarak geliştirilen açık kaynak kodlu yazılım ve sistemler özellik, kalite ve tutarlılık anlamında ticari muadillerine yetişmiş bir çok konuda da geçmiştir. Özellikle kimlik bilgileri gibi kurumsal yapılar için hayati önem taşıyan verilerin güvenliği için, kaynak kodları görülebilen ve güvenli olduğunu kanıtlamış açık kaynak kodlu sistemler bulunmaktadır. Açık kaynak kodlu Kimlik Yönetimi Sistemleri arasında kalitesi, tutarlılığı ve güvenliği ile ön plana çıkan ürün Engerek Kimlik Yönetimi Sistemidir. Sunucu üzerinde çalışan Engerek Kimlik Yönetimi Sistemi diğer kimlik veri tabanları ile doğrudan, web servisler veya “Connector” olarak adlandırılan Java tabanlı paketler ile iletişim kurmakta, okuma, yazma, silme, güncelleme gibi işlemleri merkezi ve güvenli bir şekilde gerçekleştirebilmektedir.
Erişim yönetimi noktasında endüstri standartlarını kullanan kimlik doğrulama sistemleri (SSO, CAS, Auth2.0) ile entegre çalışarak merkezi olarak doğrulama işlemlerini de gerçekleştirebilmektedir. Engerek Kimlik Yönetim Sisteminin avantajları şu şekildedir;
| Engerek Kimlik Yönetimi Sistemi | Ticari Kimlik Yönetimi Ürünleri | |
| Lisans Ücreti |  |  |
| Siber Güvenlik |  |  |
| Açık Kaynak Kodu |  |  |
| Linux Desteği |  |  |
| Destek Hizmetleri |  |  |
TÜBİTAK ULAKBİM tarafından desteklenen Engerek Kimlik Yönetim Sistemi çeşitli kamu kurumlarında kullanılmaktadır. Engerek Kimlik Yönetim Sistemi ile ilgili detaylı bilgi için Pardus ekibine ulaşabilirsiniz.