Google bu hafta başında yeni ücretsiz bir araç yayınladı. Bu araç sayesinde açık kaynak geliştiricileri projeleri ile ilgili güvenlik açığı bilgilerine kolaylıkla erişebilecekler.
OSV Scanner olarak adlandırılan Go temelli bu araç geliştiricinin kodunu ve bağımlılıklarını bilinen güvenlik açıkları listeleriyle eşleştirip, yamalar veya güncellemeler gerekirse otomatik geri dönüş sağlayan bir mekanizmaya sahip.
Yazılım projeleri genellikle birden fazla bağımlılığa sahiptir. Bununla birlikte açık kaynak paketleri diğer kütüphalerden çekilmiş çoğunlukla dökümante edilmemiş kod parçaları mevcuttur. Bu uygulama yazılımda geçişli bağımlılık(transitive dependencies) dediğimiz durumu oluşturur. Bu da manuel olarak izlemesi zor olan çok katmanlı güvenlik açığı içerebileceği anlamına gelir.
Geliştiriciler projelerinde OSV-Scanner’ı çalıştırdığında manifest’leri, SBOM’ları analiz ederek ve hashlerei işleyerek geçişli bağımlılıklarını bulmaya başlayacak. Ardından ilgili güvenlik açıklarını görüntülemek için Açık Kaynak Güvenlik Açığı (OSV) veritabanına bağlanacaktır.
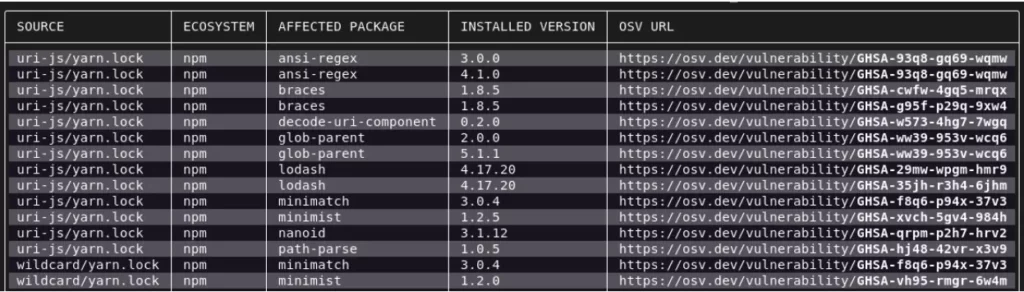
OSV-Scanner’ı şimdi deneyebilirsiniz!
OSV-Scanner’ı isterseniz yeni web sitesinden osv.dev talimatları takip ederek projelerinizde deneyebilirsiniz. Yada alternatif olarak, Github projenizde OSV-Scanner’ı otomatik bir şekilde çalıştırmak için, Scorecard‘ı kullanabilirsiniz.
Detaylı bilgiye security.googleblog.com adresinden ulaşabilirsiniz.
Projenin Github adresine github.com/google/osv-scanner üzerinden ulaşabilirsiniz.